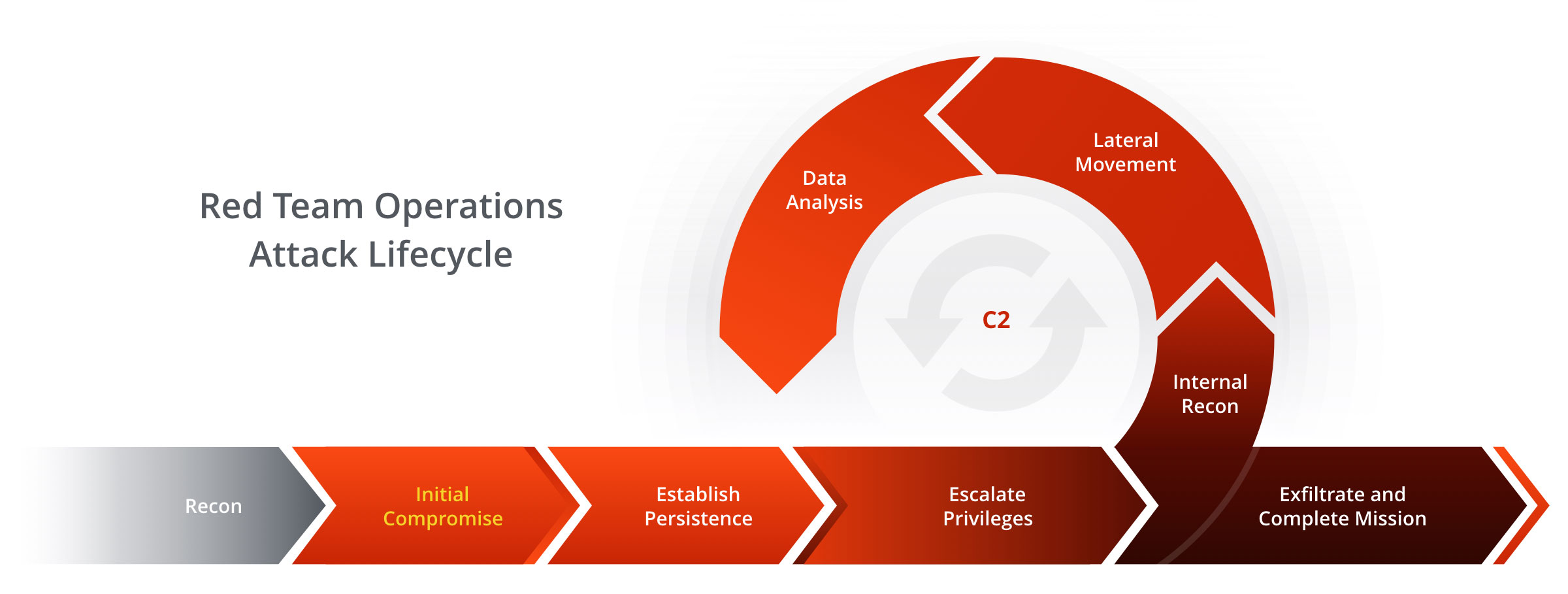
Fully assess your organisation’s threat detection and response capabilities with a simulated cyber-attack.
Learn how prepared your organisation is to respond to a targeted attack designed to test the effectiveness of people and technology
Learn whether systems, network, data and other critical assets are at risk and how easily they could be targeted by adversaries
By mirroring the latest adversarial tactics, red teaming can help identify hidden vulnerabilities that attackers might seek to exploit
Receive important post-operation support to address any vulnerabilities identified and mitigate the risk of suffering real-life attacks
By simulating a range of scenarios, red team testing helps your security team to identify and address gaps in threat coverage and visibility.
Better understand your organisation's security weaknesses and ensure that future investments deliver the greatest benefit